3 Cybersecurity Trends Businesses Must Watch Out For in 2019

2018 saw the continued rise of cyberattacks globally. 2019 is seen as a pivotal year as organizations, together with the cybersecurity community, ramp up their efforts to thwart the evolving threats and risks that cyber attackers pose. IT management platform Cloud Management Suite Director of Services Robert Brown shares his takes on what is in store for cybersecurity this year.
Just this January, the cybersecurity space was alerted to the appearance of 87 gigabytes-worth of email and password combinations on file sharing website MEGA. The data dump, now popularly referred to as “Collection #1,” contains 773 million email addresses and 21 million passwords. It has since been taken down from the sharing site.
It was later revealed to security journalist Brian Krebs that Collection #1 is just a part of a larger database of access credentials being sold online. More data dumps are available for purchase in the black market. Attackers use these email and password collections to breach other systems -- an attack known as "credential stuffing." Users typically reuse the same user names and passwords so data dumps can be used to breach accounts on other services.
The circulation of Collection #1 appears to have set the tone for cybersecurity for the year as it highlights the scale at which user data can be compromised. 2018 saw a number of high-profile security breaches including successful attacks on the systems of large enterprises like Marriott and Under Armour. Security experts expect cyberattacks to continue moving forward.
Robert Brown, Director of Services of IT management platform Cloud Management Suite (CMS), projects this year to be a critical moment in cybersecurity as he expects a continued face-off between the cybersecurity community and malicious actors. Brown shares his take on the key cybersecurity concerns for 2019 and the ways they can be addressed.
Threats will continue to grow rampant
Cybersecurity threats are likely to become even more rampant this year as IT adoption grows. Gartner estimates that global IT spending will reach $3.8 trillion in 2019.
Brown shares, "Attackers do not distinguish targets anymore. They are now bold enough to take on even large enterprises as seen in the string of breaches to networks of big-name brands last year. But even personal users can be affected. The rise in the adoption of cloud services, mobile computing, and the Internet-of-Things (IoT) by businesses and consumers has created new attack vectors. We can only expect hackers to continue searching for gaps in security to gain access to systems."
Enterprises, in particular, have become prime targets for cyberattacks as their networks and devices process large volumes of important data such as access credentials, personal and financial information of customers, and even intellectual property.
The reasons behind the attacks are varied. Some parties are motivated by profit as personal and financial data can be sold on the black market. Businesses have become willing to pay off hackers to avoid downtime and disruption of operations that these attacks can cause. Ransomware attacks, which render victims' files and systems unusable until a ransom in cryptocurrency is paid, have seen a year-on-year rise in both frequency and variety.
Espionage and even cyberwarfare are also likely causes especially when it comes to large enterprises and government networks. Large scale outages and leak of classified data can undermine militaries and economies. China and Russia have allegedly been behind the biggest state-sponsored attacks on Western targets. The Chinese were linked to the attack on Marriott and was possibly related to the ongoing trade dispute between the US and China.
An enterprise approach to security will rise
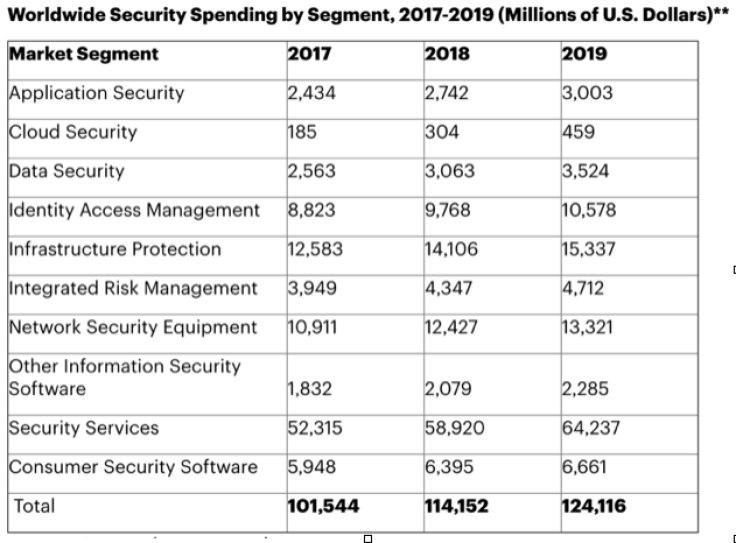
To combat threats, experts expect organizations to adopt more methodical approaches to security much like how large enterprises handle their IT. Smaller organizations and even personal users are projected to put up comprehensive strategies and adopt various security measures that allow them to mitigate and react to threats. Investments in the proper management and security tools are also expected to be made with cybersecurity spending forecasted to exceed $124 billion this year:
"Business should adopt comprehensive IT management systems that would enable them to perform audits and automatically deploy patches to all endpoints including mobile devices and IoT. They should also employ other security measures such as network and web application firewalls to prevent malicious traffic from accessing their infrastructure," continues Brown.
Organizations are seeing more endpoints connected to their networks.
"More enterprises are also allowing bring-your-own-device or BYOD schemes in their workplaces which further complicates IT security. Even a small office can now have dozens of endpoints as part of its infrastructure. Organizations must be conscious that each endpoint may contain vulnerabilities that attackers can exploit," Brown shares.
Data dumps like Collection #1 can be used to access endpoints that use these leaked credentials. Users must start using more complex passwords or use password managers that could generate unique and secure credentials.
Companies must also look outward and evaluate their third-party technology vendors and cloud service providers. As data processors, companies must check if their providers have sufficient security measures to protect their data.
Better solutions and tools will emerge
Hackers are constantly evolving their methods. Hijacked devices are used to form botnets that can automatically carry out malware deployment, credential stuffing, and denial-of-service attacks. Attackers are now also experimenting with artificial intelligence (AI) to perform more complex hacks that bypass conventional security measures.
Fortunately, cybersecurity providers are also leveraging these new technologies to create solutions and tools to fight threats. For example, Cybersecurity firm Imperva is now using AI and advanced algorithms to predict and prevent cyber threats.
Addressing the human element is also important. 52 percent of businesses believe that they are at risk from within as employees continue to be careless with technology use and expose themselves to social engineering attacks. Fortunately, businesses are also keen on putting up onboarding and training programs that equip staff with the proper competencies to manage their use of IT resources.
Given the frequency of attacks, stakeholders must also be able to act with urgency.
"Timely knowledge of developing threats will become all the more critical. Security professionals and developer communities must work together to understand emerging threats. Developers must also be quick to advise users on discovered vulnerabilities and promptly release fixes so that companies will be able to act before anything adverse happens. In our case, we're working on a real-time security feature on CMS that allows administrators to execute commands using plain language and stop breaches as they occur. This way, fixes can be deployed without the need to key in complex code or instructions," comments Brown.
Security not an option
Businesses are bound to face increasing pressure to secure their infrastructures this 2019. Aside from threats from malicious actors, they now also face scrutiny from users who are now more discerning about how their data are used and protected by the companies with which they transact. Businesses have no choice but make security a core part of their operations.
In addition, data protection laws like the GDPR place concrete guidelines on how companies should protect customer data. Non-compliance even exposes businesses to further losses due to the significant fines that these regulations impose on violators. For a global enterprise, the GDPR can exact a percentage of global revenue amounting to billions of dollars.
"Companies must put cybersecurity at the forefront of their business strategies. Knowing these key trends should help them make the right decisions and work towards securing their infrastructures," Brown concludes.






